Thursday 29 November 2007
Welcome to the world of virtualization: vmware
Solution: Vmware virtulization.
What is virtulization:
The software layer providing the virtualization is called a virtual machine monitor or hypervisor.
Its basically a emulated set of hardware, they just give u virtual hardware environment, you need to install the real operating system and real application. They dont give u packed-up vesion of OS, no, they are not giving you virtual OS, its virtual hardware . Iam here talking about the vmware-workstation product. They just take the existing hardware and present to you as new set of hardware (virtual) , you need to install the real OS and applications on top of it.
Note: Applications & OS are real, only hardware is emulated.
With vmware, you can have multiple applications in your single machine, independent of each other, each application has its own OS and own set of virtual hardware. virutal hardware is identical where ever you go, virtual machine can be moved from machien to machine , b'cos of the hardware independece between the virtual machines.
Virtual hardware:
CPU:CPUS is something they dont emulate, CPU is allocated to different virtual machine, therefore they pass the instruction directly through from guest OS (virtual machine) down to the physical processor.
Memory: Memory is something they don't emulate, , memory is allocated to virtual machine, but the instructions are again sent thru to physical memory but, they do emulate all the other hardware like :Network card, serial & parallel ports, cdrom, floppy drive ,key board, mouse etc.
Now, with vmware , you can have multiple applications on the single host OS, b'cos they have their own virtual hardware, own protected memory and own environment, independent of other virtual machines. They are completely isolated machines, if anything happend to one virtual machine ,it does not affect the other virutal machine or the host OS.
Real world problem : You have a OS, which has complete control over the hardware, which then parcels out the resources to one or more applications. There are two problems with this ,which hurts the management of this system.
Application is completely dependent on OS configuration, different Applications means different service packs, OS service packs, and they can even crash the hardware if they misbehave with the OS, and they could misbehave in terms of driver, service packs, etc. Different applications shares the same hardware, so they can not work well together.
Os is tied to the hardware, thru its driver, kernel, because of its dependence on the hardware, it can not be moved easily, where as vmware virtual machine is basically a "file", therefore it can be moved to another mahine in matter of seconds, b'cos of its hardware indepedence across all hardware platform , across all os, the vmware emulated hardware remains the same.
Feature : Paritioning
1. Run multiple OS on one physical machine.
2. Fully utilze server resources.
3. SCSI reservations enable clustering.
Feature: Isolation & Workload Management
1. Key: Uses CPU harware (Protection)
2. Fault, performance, and security isolation.
3. CPU, RAM, Disk, and network resource controls.
Feature: System Encapsulation
1. Entire state of the VM is encapsulated: (Memory, disk images, I/O
device state)
2. VMs state can be saved to a file: (Checkpointing, aka "suspend/resume"
3. VM state can be transfered thru time and space :(Time: Store in a file, Space: Transfer over a network)
For more information on this cool technology, you can visit: http://www.vmware.com/
Friday 17 August 2007
What is GRUB, it is the first thing you see When you boot Solaris, Redhat or other UNIX-like distro..
GRUB is currently available under the GNU General Public License as "free" software, free to share and change. Project was launched in line of creating a free 'boot loader'.
GRUB: GRUB orginated in 1995, when Enrich Boleyn was trying to boot the GNU Hurd with the University of Utaha's Mach 4. Enrich then began modifying the FreeBSD boot loader, so that it would understand Multiboot. He soon realized that it would be lot easier to write his own boot loader from scratch than to keep working on the FreeBSD boot loader, and so GRUB was born.
GRUB:(GRand Unified Bootloader), is a boot loader package from the GNU Project, it allows a user to have several different operating systems on their computer at once, and to choose which one to run when the computer starts. GRUB can be used to select from different kernel images available on a particular operating system's partitions, as well as to pass boot-time parameters to such kernels.
GRUBcan run on any operating system with a Multiboot kernel. It is predominantly used on Unix-like systems; the GNU operating system uses GNU GRUB as its boot loader, as do most general-purpose Linux distributions. Solaris has been able to boot using GRUB since version 10 (1/06 release).
GRUB: (Features)1. Basic funtions must be straightforwad for end-users.2. Rich functionality to support kernel experets and designers.3. Backward compatibility for booting FreeBSD, NetBSD, OpenBSD, and Linux . Proprietary kernels such as :a. DOS.b. Windows Nt.c. OS/2 ,
Are supported via a chain-loading fuction.
Courtesy:www.gnu.org
Wednesday 15 August 2007
Linux is a "KERNEL" not an Operating System :
For the past one year, i have been working with UNIX-like distros.., but i never give it a thought to know the difference between a "kernel" which is a linux and the Operating System which is a GNU, untill i came across a document by Richard Stallman, that corrected my "wrong" assumption of Linux as OS.
http://www.gnu.org/gnu/linux-and-gnu.html,
So, what is Linux:
Friends, Linux is just a "kernel", it can only function in the context of a complete operating system.( Kernal definition: The program in the system that allocates the machine's resources to the other programs that you run).
The "kernel" is an essential part of an operating system, but useless by itself; it can only function in the context of a complete operating system. Many users are not fully aware of the distinction between the kernel, which is Linux, and the whole system, which they also call “Linux”.
In simple layman words:
GNU an "UNIX-LIKE OS" was already created as a complete OS, with "Hurd" as a kernel in early 1990, but there were few problems with this kernel and it was still being developed, fortunately , it was during 1991, when "Linus Torvalds" wrote Linux (Free Unix like Kernel) and filled the last major gap, and that's all about it, Linux (kernel) together with the GNU system gave brith to a complete free Operating System called "GNU/Linux".
What is GNU:
If you are wonderfing what is "GNU", here is the information :GNU stands for “GNU's Not Unix. GNU is a project by community of people, conceived in 1983 as a way of bringing back the cooperative spirit that prevailed in the computing community in earlier days—to make cooperation possible once again by removing the obstacles to cooperation imposed by the owners of proprietary software, the main object was to create "FREE" software.
By "Free" it means:
Software that comes with permission for anyone to use, copy, and distribute, either verbatim or with modifications, either gratis or for a fee. In particular, this means that source code must be available. “If it's not source, it's not software.
Courtesy: Richard Stallman
Friday 10 August 2007
Love Linux not necessarily marry !
When I say love Linux, I actually meant, experience it, see the difference yourself, and then decide what you want to do, I think that's a fair statement . To being with, you can either have it installed on the other partition of your PC so that you continue to use the existing OS and yet get the taste of Linux. In case you do not want to part ways with your Hard disk for whatever reason, you can get a copy of VMWARE application (http://www.vmware.com/) installed on your system and run the virtual image of Linux, this is what i have been doing for past one year, this tool gives you the freedom to use/test different types of Linux distros.
Like most of us, i always feared of UNIX-like OS, b'cos of its resemblance with UNIX, and i always imagined UNIX administrators running through complex commands via command line interface , and i always asked myself, without any knowledge of commands, how am i going to find and run my favorite applications, how am i going to deal with listening to audio or watching movie, these were some of my fears when i thought of UNIX from a beginners point of view.
I googled and found lot of stuff about Linux, soon I got to know that, there are Desktop packages that gives you Desktop-Environment similar to Windows so that you can easily work through your Linux, A “desktop environment” can mean anything ranging from a simple window manager to a complete suite of desktop applications, such as KDE or GNOME.
So, Solaris / Redhat / Ubuntu.. all can have a desktop :) , for this article, we shall only concentrate on one such application called GNOME:
What is GNOME:
Acronym for GNU Network Object Model Environment. (Pronounced guh-nome.) GNOME is part of the GNU project and part of the free software, or open source, movement. GNOME is a Windows-like desktop system that works on UNIX and UNIX-like systems and is not dependent on any one window manager. The current version runs on Linux, FreeBSD, IRIX and Solaris. The main objective of GNOME is to provide a user-friendly suite of applications and an easy-to-use desktop.
http://en.wikipedia.org/wiki/GNOME
In case you want to work from command-line, no one is stopping you : Just open the "Terminal", and play with commands if your main purpose is to deal in commands. That's it, i installed redhat, and got familiar with the look of it, what is where etc, but i must say, its so quick and easy to work through commands, and it is not tough, its just a matter of getting use to, i googled to look for article on the web and found of millions of page dedicated to Linux forums where you can get direct help from other Linux users, i slowly started working with commands, and in the process, i learnt , how to "unzip" (gunzip) file in Linux, what is "Kernel" , "Directory structure" , "daemons (Programs) " ,"services", "Libraries" , "tar" , what is "package", how to move/ copy/ delete / edit / how to setup FTP etc . It was slow process, but i did not mind b'cos my Job did not depend on it, I was learning it as a hobby, which indeed made me more relax and patient and that helped me in digging further in to "UNIX commands".
Over the past year, since i first saw the Linux, i have worked on Redhat, Ubuntu and Solaris and believe me, most commands work the same on these different flavors, therefore handy UNIX commands will help you any day on any flavors. For those who are least interested in commands, and just looking for more reliable, bug free environment and yet wants to retain the user friendly features of Windows can always work with window managers provided by KDE/GNOME.
I still consider myself a novice here, but that does not mean complexity on the Linux side , i just like to be like that, Linux is a journey for me not a destination , discovering virus free environment where my PC not only works faster than before it even runs similar applications like Office (word, excel, power-point) which i have been use to for ages. Further, you never know when this extra bit of skill will come handy at your current job space, or even lend you a better job than the one you currently have. So, why shy away, go ahead and befriend Linux.
We all feel good, when we work through command line, don't we ;) , even though same can be achieved via GUI, because that lifts our confidence in the command-line world . On this point let me introduce you to what is called :Terminal, command line, Shell etc.
The command line is also known as the terminal or the shell. People also call it a terminal window, or a shell prompt, or a command prompt.
Terminal window = command prompt = shell , its one and the same.Running a command, means typing something at the command prompt then pressing the ENTER key to execute the command.
Let's take a look at some of the basic commands that are the most useful:
1. View directory contents with 'ls'
'ls' command, the purpose of this command is to list the files that are in the current directory. At the command prompt, type in 'ls' without the quotes. Then press the ENTER key. You will see a list of files that are in the current directory. Let's look at an example of how to use this command:
user@linux~> ls
2. Make a directory with 'mkdir'How can we create a directory? There is a command called 'mkdir' that is used forthis. You use this command using this as a pattern:
mkdir [insert directory name here]
3. Remove a directory with 'rmdir'Once we have made a directory, can we remove it? Yes. We use the 'rmdir'command. This command is similar to the 'mkdir' command in regards to how to useit:
rmdir [directory you want to remove]
You just replace the "[directory you want to remove]" with the actual name of the directory you want to remove. For example:user@linux:~> rmdir myfiles
4. Change to a directory with 'cd'
Let's say that we have just created a directory called 'myfiles'. How do we then go into that directory? This is what the 'cd' command is for. It is used to "c"hange"d"irectories. This is how we will use this command:
cd [directory name]
How do we get back out of the directory? Instead of providing a directory name,we just put in two dots for the name. This just means, "I want to leave the directorythat I am currently in." This is what using the command looks like:user@linux:~/myfiles> cd ..
5.What directory am I in? Using 'pwd'
How do we know what directory we are in? There is a very simple command forthis. It is called 'pwd'. That just means "p"resent "w"orking "d"irectory. You use itlike this:
pwd
And it tells you what directory you are in. Using this command will help youknow if you are in the right place.
6. Copying files with 'cp'
Now that we know some commands for working with directories, let's look atsome ways to work with files. To begin with, we will look at copying a file. Thecommand 'cp' will do this for us. Its usage is thus:
cp [source file] [destination file]
You just replace "[source file]" with the file you want to copy. You replace the"[destination file]" with the place you want that file copied to. For example, if I hada file called 'mybooks.txt' and I wanted to make a copy of it called 'somebooks.txt', Icould run this command:
user@linux:~> cp mybooks.txt somebooks.txt
7. Moving files with 'mv'
If you want to move a file instead of copy it, you can use 'mv'. The syntax ofhow to use this command is very similar to the 'cp' command:
mv [source file] [destination file]
Replace "[source file]" with the name of the file you want moved. Replace "[destination file]" with the filename you want it moved to. You may notice that you can also use this command to rename a file, "moving" it from one filename to another. Example:user@linux:~> mv myfile.txt yourfile.txt
8. Deleting files with 'rm'
What about if we want to delete a file? This is the purpose of 'rm'. Thiscommand will permanently remove a file, so be careful with it. The way you use this is as follows:
rm [file to delete]
Again, use caution with this command. Its effects are permanent. Here is anexample:user@linux:~> rm myfile.txt
9. Viewing text files with 'cat'
Many files in Linux are text files. How do we view the contents of such textfiles? If the file is relatively small (its contents won't fill up more than one screen),we can use the 'cat' command. This command will just output the contents of the filestraight to the screen. Its usage is as follows:
cat [filename to display]
10. Viewing text files with 'less'
What if the file is too long to fit on one page? If it is a really big file, it may justdump large amounts of text to your screen. This will make it scroll up way fasterthan you can read it. Is there a solution to this problem? You bet. It is the 'less'command. This is how you use it:less [filename to display]
11. What time is it? What is the date? Using 'date'One very easy command is called 'date'. This displays the current date and time.Use this command as follows:
date
In addition to these commands, Sometimes, you will runinto a situation where you may need some help learning how to use a particular command. Fortunately, there is a help system built into Linux which can assist you with this. It is the 'man' command, which displays help on using other commands.
Using 'man' to find help
To use 'man', the following is the syntax:man [command]
Saturday 4 August 2007
Installing Samba on Solaris:
Samba is supplied in source form and you need to compile it. This isn't difficult! Before doing so, you need to have installed the g(un)zip program and a C compiler. All of these are freely downloadable from the Net and instructions for installing C and gzip are here.
Step by Step procedure:
http://www.kempston.net/solaris/samba.html
The source code of Samba is available from:
http://samba.org/
Friday 3 August 2007
What is Telnet and SSH?
Telnet and SSH allows you to access your shell account.
Are there any differences between TELNET and SSH?
TELNET and SSH has long been employed by end-users and system administers to remotely control his or her servers. The key differences is that TELNET establishes a plain text connection while SSH, or Secure Shell, uses an encrypted connection so no one can ears drop on what data is being received or sent.
If you need to connect to the web server hosting your web site then SSH is the better option of the two since security is always a major concern, particularly, for businesses. Also, you do not want to legally liable for any damage that may occur from your web hosting account being used for illegal activities.
Why SSH?
As you might imagine, this increases your security significantly.
Port (Ftp): 20 & 21
Where can I get an SSH client? (For Windows Platforms)
2. Can I run backups over ssh?
Yes. The easiest possible way to do this is:
# tar cvf - ssh user@host "dd of=/dev/tape"
3. Can I use ssh to communicate across a firewall?
Set up the remote daemon running sshd on port 443:
# sshd -p 443
Then, on your local system, open a connection on port 443:
You can also use Secure Shell to tunnel insecure traffic like POP, IMAP, and others through the firewall as well.
Sunday 24 June 2007
Difference between BLOCK and FILE level Data : -Ashwin
SQL and Exchange: Are highly write and read intesive databases, in other words, they need faster processing because they process many read and write requests, (Online Transaction Processing) and thats why they deal in "Blocks". Therefore SQL and Exchange database is not recommended on "NAS" or "FIle servers", because these file servers are usually accessed as a mapped or UNC path and the data is moved via "TCP/IP" network and it deals in "File Level" protocol such as "CIFS/SAMBA" for Windows and NFS for (UNIX/Linux) paltforms which is not suitable for Databases applications.Block storage is normally abstracted by a file system or database management system to talk to clients or endusers.
Block based databases requires : Locally attached disk array Or SAN data centers.
File Level Data: The data which has file system attached, for example: a word document , is a file level data and is backedup along with this meta data. This is where NAS / Netapp / Windows Storage Server comes in to picture, they are basically "Read" intesive boxes. They are not meant for intensive writing, they are basically file servers providing file service (Read) to clients. For normal disk sharing between small Office / Home office this is a good option, where many users can write to and read to common "Disk" on the remote server via mapped or unc path.
File level : NAS / Netapp & Windows Storage Server.
Summary:
This file system can reside either on a server or on a NAS device. If it’s on the server, block level data is written to the disk array, usually via either an FC or iSCSI interface. If the file system is on the NAS, file level data is written to the NAS device, usually via Ethernet. The NAS device in turn writes block level data to disk. A “NAS Gateway” is a device that maintains the file system and communicates file-level data with clients on the LAN, while storing data on external FC-attached disk.
An advantage of file level data is the ease of sharing information. Because the file system resides within the NAS, any device can access and understand the data. When the file system resides in the server, only that server can retrieve data from the disk.
BLOCK vs FILE - WHAT HAPPENS UNDERNEATH
Affordable Windows iSCSI storage area network : Backup Exec backs up data to ISCSI drive.
How to build an affordable Windows iSCSI storage area network, Here in this article, author has shown, how Backup Exec for Windows Server can make use of "NAS" Or another Server's Hardisk as backup drive and transfer data "Block-Level" via "ISCSI" protocol. This is faster than the orthodox "TCP/IP" file-level backup.
Courtesy:
http://www.crn.com/article/printableArticle.jhtml?articleId=59201007
Wednesday 20 June 2007
Interview questions for tech companies : Crack it.
http://www.techinterviews.com/
It's a wonderful site for those who are prepraring or in process on any forthcoming interview schedule. You can find interview related question's ranging from :
1. Exchange Domain
2. Databases.
3. Backup Administrator
4. Computer Hardware.
5. Testing.
6. Developer (C++, Java etc)
7. Networking.
Any, many more.
Courtesy: http://www.techinterviews.com/
Monday 18 June 2007
NDMP ended the monopoly of the Backup software Vendors and File Server vendors :
for ex:
1. Windows agent for Windows Servers.
2. Unix angent for Unix/Linux Servers.
3. Solarix agent for Solaris Servers.
4. Mac agent for Mac Servers.
This not only led to more cost incur on the vendor side for development of these agent, but also customers had to bear the cost of so many agents, further dedicated file servers had to be mounted to such OS so that their data could be backed via NFS or CIFS (SAMBA) file level protocols. Most serious drwabacks were , data had to travel via networks to the central backup application where "tape/library" was attached.
Thursday 14 June 2007
FIler Definition: -Ashwin
Backup and Restore : By Dilip Naik
Backup and Restore Technologies:
http://searchstorage.techtarget.com/
searchStorage/downloads/Naik_ch05.pdf
Friday 25 May 2007
VMware Infrastructure 3 Demo: Magical Suite for IT People / Department.
Features:
1. Running number of Virtual servers off the fewer Physical Server.
2. Run different OS off the same Physical Server, its hardware independent.
3. You can build Virtual Web-Server, straight on the fly.
4. You can create many test setups, straight on the fly using the templates.
You can watch this video right here,
Wednesday 23 May 2007
Linux Filesystem Hierarchy - Part One , From Binarysignal
Monday 21 May 2007
BAD PASSWORD: it is based on dictionary word | Linux password issues | -Ashwin
 The most reliable way to change your linux password is via a command prompt. You will need to start a terminal window. At the prompt, type passwd. You will be prompted to enter your current password, followed by the new password and the new password again. None of the passwords will be echoed on the screen.
The most reliable way to change your linux password is via a command prompt. You will need to start a terminal window. At the prompt, type passwd. You will be prompted to enter your current password, followed by the new password and the new password again. None of the passwords will be echoed on the screen.If you do not see the message "authentication tokens updated successfully" there was an error changing the password. Just type passwd and try again. Pay careful attention to your typing.
You may get some errors: As shown in the Figure above .
BAD PASSWORD: it is based on a dictionary word
That means your password doesn't meet the password requirements. Ideally it should be at least eight characters long, not based on a dictionary word and a mixture of letters, numbers and characters.
Solution: Incase you don't have time to think of any possible good password, make use of the "Online" password generator, the link is given below.
Saturday 19 May 2007
Penguin Gallery : Funny, Cute and artistic penguins...
 Super-Penguin , Here is a collection of the interesting penguins we have been able to find out there on the net. Note that we're not trying to gather up every occurence of a penguin somewhere - the idea here is to catalog the "derivative" penguins that are on the loose. Please click on the web URL given below to see penguins in different imagination.
Super-Penguin , Here is a collection of the interesting penguins we have been able to find out there on the net. Note that we're not trying to gather up every occurence of a penguin somewhere - the idea here is to catalog the "derivative" penguins that are on the loose. Please click on the web URL given below to see penguins in different imagination.In the beginning, sometime in early 1996, several people were talking on the linux-kernel mailing list about a suitable logo/mascot for Linux. Of the many, many suggestions, many involved parodies of other operating system logo's - or were strong, noble beasts such as Sharks or Eagles. At some point (I'm not sure when), Linus Torvalds (the father of Linux) casually mentioned that he was rather fond of Penguins - which rather stopped the debate in its tracks.
Penguins Gallery:
http://lwn.net/Gallery/
Penguin the Linux Mascot : Story goes like this..
 Linus Torvalds, the creator of the Linux Kernel, was visiting his friend Andrew Tridgell, the creator of the Samba suite. They were walking through the Zoo in Canberra when, without warning, a huge flock of vampire attack penguins dove out of the sky and tried to carry Linus away. Fortunately, Andrew had an umbrella. Still, one of the birds was able to nip Linus' hand with its fanged beak. Rumor has it that on moonlit nights Linus still runs out into the darkness and jumps, stark naked, into icy water. Of course, he's Finnish and may always have done this. In any case, this is why the Penguin is the Linux Mascot.
Linus Torvalds, the creator of the Linux Kernel, was visiting his friend Andrew Tridgell, the creator of the Samba suite. They were walking through the Zoo in Canberra when, without warning, a huge flock of vampire attack penguins dove out of the sky and tried to carry Linus away. Fortunately, Andrew had an umbrella. Still, one of the birds was able to nip Linus' hand with its fanged beak. Rumor has it that on moonlit nights Linus still runs out into the darkness and jumps, stark naked, into icy water. Of course, he's Finnish and may always have done this. In any case, this is why the Penguin is the Linux Mascot.Why Penguins?
This email from Linus in response to this very question seems to explain the significance of the Penguin:
Letter goes like this:
Re: Linux LogoLinus Torvalds (torvalds@cs.helsinki.fi)
Sun, 12 May 1996 09:39:19 +0300 (EET DST)
Umm.. You don't have any gap to fill in.
"Linus likes penguins". That's it. There was even a headline on it in some Linux Journal some time ago (I was bitten by a Killer Penguin in Australia - I'm not kidding). Penguins are fun.
As to why use a penguin as a logo? No good reason, really. But a logo doesn't really ave to _mean_ anything - it's the association that counts. And I can think of many worse things than have linux being associated with penguins.
Having a penguin as a logo also gives more freedom to people wanting to use linux-related material: instead of being firmly fixed with a specific logo (the triangle, or just "Linux 2.0" or some other abstract thing), using something like a penguin gives people the chance to make modifications that are still recognizable.
So you can have a real live penguin on a CD cover, for example, and people will get the association. Or you can have a penguin that does something specific (a Penguin writing on wordperfect for the WP Linux CD, whatever - you get the idea).
Compare that to a more abstract logo (like the windows logo - it's not a bad logo in itself). You can't really do anything with a logo like that. It just "is".
Anyway, go to "http://www.isc.tamu.edu/~lewing/linux/ for some nice examples..
Linus
Courtesy:
SAMBA Permission Vs Linux Permission: Who takes precedence
Few things about Linux and Samba permissions:
1. Linux system permissions take precedence over Samba permissions. For example if a directory does not have Linux write permission, setting samba writeable = Yes , will not allow to write to shared directory / share.
2. The filesystem permission take precedence over Samba permission. For example if filesystem mounted as readonly, setting writeable = Yes will not allow to write to any shared directory or share via samba server.
How do I set permissions to Samba shares? Samba Basic permissions are as follows (configuration file is smb.conf [/etc/samba/smb.conf]):
1. Read only: This parameter controls whether an user has the ability to create or modify files within a share. This is default.
2. Guest ok: Usually this parameter is set to yes, the users will have access to the share withouthaving to enter a password. This can pose security risk.
3. Writeable: Specifies users should have write access to the share.
You can create the share called helpfiles with read only permission
[helpfiles]
path = /usr/share/docs
read only = Yes
You can create the share called salesdoc with write permission
[salesdoc]
path = /home/shared/sales
writeable = Yes
You can also create a list of users to give write access to the share with write list option. For example allow rocky and tony to write to the share called sales:
[salesdoc]
path = /home/shared/sales
write list = rocky tony
You can use following options:
Read list: This option accepts a list of usernames or a group as its value. Users will be given read-only access to the share.
Valid users: You can make a share available to specific users. Usernames or group names can be passed on as its value.
Invalid users: Users or groups listed will be denied access to this share.
Samba mask permission :
It is also possible to specify samba default file creation permission using mask.
create mask: This option is set using an octal value when setting permissions for files. directory mask: Directories must have the execute bit for proper access. Default parameter is 0755.
[salesdoc]
path = /home/shared/sales
write list = rocky syscreate mask = 0775
Courtesy: VIVEK
http://www.cyberciti.biz/tips/how-do-i-set-permissions-to-samba-shares.html
Friday 18 May 2007
New Samba 4.0 targets Active Directory
Releasing a new version of the software today in conjunction with a speech on the subject by Australia-based Samba creator Andrew Tridgell at the Linux.conf.au conference in New Zealand, the team behind the software outlined its new features.
"Samba 4 supports the server-side of the Active Directory logon environment used by Windows 2000 and later, so we can do full domain join and domain logon operations with these clients," the group said in a statement on its Web site, noting this feature was "the main emphasis" for the new software.
"Our domain controller implementation contains our own built-in LDAP (Lightweight Directory Access Protocol) server and Kerberos key distribution centre as well as the Samba 3-like logon services provided over CIFS," the statement continued.
The Samba developers noted their implementation of Kerberos correctly dealt with the "infamous Kerberos PAC (Privilege Access Certificate)" -- a data field in the Kerberos authentication protocol which attracted controversy when critics claimed that Microsoft's version tied users into its own version of Kerberos.
Other improvements include the integration of Samba's Web-based administration tool (SWAT), a new scripting interface which allows Javascript programs to interface with Samba's "internals", and new Virtual Filesystem (VFS) features.
Also, "the Samba 4 architecture is based around an LDAP-like database that can use a range of modular backends". "We are aiming for Samba 4 to be a powerful front end to large directories," said the statement.
Courtesy:http://www.zdnet.com.au/
Learning Tutorials: Linux | UNIX | Networking
http://networking.ringofsaturn.com
networking.ringofsaturn.com/Unix/unixguide.php
Compiling the Linux Kerenel
http://networking.ringofsaturn.com/Unix/linux-kernel.php
How Network Traffic Flows – Getting Started
http://networking.ringofsaturn.com/IP/howtrafficflows.php
What is routing?
http://networking.ringofsaturn.com/IP/Routing.php
IBM ENTRY SAN: DS3000 Series, is a S.A.F.E.R option
A:Affordable :Excellent Value
F:Flexible: Can attach to System x, BladeCenter and 3rd Party servers. Best for mixed-server vendor enviornment.
E:Easy : DS3000 Storage Manager software makes deployment & installation simple
R:Reliable : IBM quality
Watch Video:
http://youtube.com/watch?v=Kbb7xQACWxw
Wednesday 16 May 2007
What is Samba? -Ashwin
Samba is an open source software package that mimics a Windows server. Its purpose is to offer an alternative to expensive, unstable Windows servers. Samba can replicate nearly all of Windows server functionality. It appears in the Network Neighborhood like any other Windows machine and functions in the same way. In fact, some servers on your network right now could be running Samba instead of Windows and no one would ever notice.
Samba essentially consists of two or three daemons. A daemon is a UNIX application that runs in the background and provides services. An example of a service is the Apache Web server for which the daemon is called httpd. In the case of Samba there are three daemons, two of which are needed as a minimum.
1. nmbd : Daemon acts as a WINS server service providing DNS-like name-to-IP address translations.
2. smbd : Daemon is the core Samba server service which enables file and printer sharing, network browsing, etc.
winbindd: (3rd Daemon)
This daemon should be started when Samba is a member of a Windows NT4 or ADS domain. It is also needed when Samba has trust relationships with another domain. The winbindd daemon will check the smb.conf file for the presence of the idmap uid and idmap gid parameters. If they are are found, winbindd will use the values specified for for UID and GID allocation. If these parameters are not specified, winbindd will start but it will not be able to allocate UIDs or GIDs.
SAMBA shell script resides in following dir:
/etc/init.d/samba
The main Samba configuration file called smb.conf and is located in this directory:
/etc/smb/samba.conf
Warning: Make sure you backup this file, before making any alterations. Use this command:
cp /etc/samba/smb.conf /etc/samba/org-smb.conf
The smb.conf file supplied with most linux distributions has six sections:
1. [global] - contains many subsections for network-related things such as the domain/workgroup name, WINS, some printing settings, authentication, logging and accounting, etc.
2. [homes] - for file sharing of user home directories
3. [netlogon] - commented out by default, for setting the server to act as a domain controller
4. [printers] - for printer sharing of locally-attached printers
5. [print$] - to set up a share for Windows printer drivers
6. [cdrom] - commented out by default, to optionally share the server's CD-ROM drive
I have only edited following section for my sharing:
[global]
Workgroup = Redhat-SAMBA
Server String = Samba Server
hosts allow = 1.1.1.8
encrpt passwords = yes
smb passwd file = /etc/samba/smbpasswd
[files]
comment = Shared Files
path = /myshare
writeable = yes
Browseable= yes
Valid users=username
Note: I presume , both Windows and Linux box can see/ping each other. Minimum requirement. It is advisable to add the netbios name entry in each other machine.
For Example:
Here is my /etc/samba/lmhosts file
windows machine IP address
And here is my /etc/hosts file:
Linux machine IP address
To configure Samba on your Red Hat Linux system to use encrypted passwords, follow these steps: If someone needs to access a share on your Samba server, they must be both a valid user of the system and a valid Samba user.
Adding Users to a Linux System
To add users to a Linux system, use the following command:
adduser
For example, to add user ashwin to the system, execute the command
adduser ashwin
After adding the user, specify a password for them with the command
passwd
For example to change ashwin password execute
passwd ashwin
Adding Samba Users
To add users to the Samba users list, execute the command
smbpasswd -a
For example, to add ashwin , execute the following
smbpasswd -a ashwin
That's it, now start the SMB service and reload the smb.conf file.
To start smb service:
/etc/rc.d/init.d/smb restart
or
# smb service restart
To reload smb.conf file:
/etc/rc.d/init.d/smb reload
or
# smb service reload
Finaly in Windows Machine:
Open the Windows machine Go to Mynetworkplaces Entire Network Microsoft Windows Network and You should find the "SAMBA" server. You can decide what workgroup name you want to give in the smb.conf file.
Courtesy: Samba: An Alternative to Windows Servers
http://www.mcsr.olemiss.edu/bookshelf/articles/Samba.html
http://samba.org/samba/docs/man/Samba-HOWTO-Collection/install.html
Thursday 10 May 2007
15 years Linux: past and future (video)
Sun Fire x4500 demonstration:
Hardware-related questions about Complete PC Restore :
Q. Can you restore a Complete PC Backup image to a smaller drive if the amount of space used in the initial backup is smaller than the smaller disk?
A. The backup can be restored only if:
At least the same number of hard drives are present, and
Each disk is at least as big as the disk it replaces.
Here are some examples to illustrate this:
Working examples
During backup
---------------------------------
1x100GB drive
1x100GB drive
1x100GB drive
1x100GB drive,1x200GB drive
1x100GB drive,1x200GB drive
During restore
--------------------------------
Non-working examples
During backup
----------------------------------------------
1x100GB drive
1x100GB drive
1x100GB drive
1x100GB drive, 1x200GB drive
1x100GB drive, 1x200GB drive
1x100GB drive, 1x200GB drive
*possibly due to no drivers loaded in Windows Recovery Environment (RE)
Courtesy: cfsbloggers
http://blogs.technet.com
Saturday 5 May 2007
Practical approach to ISCSI: - My personal views & understanding. - Ashwin
 Is I-SCSI an Software Or Hardware ?
Is I-SCSI an Software Or Hardware ?Still confused ? , well the answer is, its in both forms, as explained below.
I-SCSI can be thought as client-server architecture.
A "client" (ie: your system - OS) is an initiator, it initiates requests."
A "server" (ie: your storage device - Disks) is a target.
1. ISCSI- Initiator (Free download available)
2. ISCSI- Target (Free download available, NOT all vendors)
A software initiator and Target is just a driver that handles all requests and pairs the network interfaces driver and the SCSI drivers together to make it all work.
Bottom Line: There is no cost involved in using a software initiator and Target (Though some Vendors has price tag for target sofware ) . Disadvantage may be: High CPU usage on Host due to processing of TCP/IP + SCSI Commands.
I-SCSI Hardware Package includes:
1. ISCSI- HBA as Initiator as shown in pic above.
2. ISCSI- HBA as Target as shown in pic above.
Hardware Card is nothign but a ethernet card with a SCSI ASIC on-board to offload all the work (TCP/IP + SCSI processing) from the system CPU.
Note: Each iSCSI HBA adapter has two IP addresses: one for SCSI and one for LAN.With iSCSI HBA, TCP/IP and iSCSI protocol processing may be performed on an embedded processor.
Thank You, views from technical gurus are welcome.
FYI: With due courtesy to following sites.
Reference: (Courtesy:http://www.snwonline.com/implement/isci_feasible_04-15-2002.asp)Reference: (Courtesy:http://www.cuddletech.com/articles/iscsi/index.html)
Reference(Courtesy:http://www03.ibm.com/systems/i/
bladecenter/flash/iscsi_systemx_install.swf)
Thursday 3 May 2007
I-SCSI network , really cool concept. It has scalability and capability.-Ashwin
Theory: iSCSI Protocol Concepts and Implementation
http://www.cisco.com/en/US/products/hw/ps4159/ps2160/
products_white_paper09186a00800a90e4.shtml
Installation Sofware:
I-SCSI Initiator:
You can get the iSCSI Initiator from the Microsoft download website:
Courtesy:
http://www.microsoft.com/downloads/details.aspx?familyid
=12CB3C1A-15D6-4585-B385-BEFD1319F825&displaylang=en
I-SCSI Target:
Download FREE StarWind iSCSI Target evaluation version 3.2.2 from following link:
Courtesy:
http://www.rocketdivision.com/download_starwind.html
You can even watch a video on I-SCSI setup:mms://wm.microsoft.com/ms/inetpub/keithcombs/iSCSI.wmv for the iSCSI demo.
Courtesy: Keith Combs
http://blogs.technet.com/keithcombs
Four Stages to implimenting iSCSI :Courtesy:
http://www.iscsi-storage.com/iscsi_stages.htm
Microsoft Storage Technologies - iSCSI
http://www.microsoft.com/windowsserver2003
/technologies/storage/iscsi/default.mspx
Tuesday 1 May 2007
what the hell is i-SCSI ? -Ashwin

When i first heard this term two years back , i thought it is "Ice-SCSI", it sounded like that, and for no reason i felt it is something complicated technology and my assumption was quite natural and i guess every individual have certain assumption on the way technical term sounds, though my theory of assumption is ridiculous but let me tell you its not complicated.
Coming back to "What is I-SCSI" ? , let me try to explain in the less complicated manner.
I-stands for Internet and SCSI as you know stands for Small Computer System Interface. SCSI deals in "Blocks" and Internet deals in "Packet" i.e IP Packet. Here both SCSI and Ethernet technology work together to perform SCSI Data transfers over TCP/IP networks.
It basically allows the block storage SCSI commands to be carried by the standard TCP/IP protocols over the Ethernet wire.
Until recently, Ethernet was too slow to compare to the performance of direct attach storage. With the advent of 1 Gigabit and 10 Gigabit Ethernet, an Ethernet network is now fast enough to use for storage applications.
Technically, this is how it works:
Basically, iSCSI is composed of "initiators" and "targets" that will be used at both ends of the Ethernet wire. The iSCSI initiator connects the computer that initiates the request for data stored on the disk with the Ethernet wire. The iSCSI target connects the Ethernet wire with the storage device, whether it be an array of disks or perhaps a tape device. The initiator encapsulates the SCSI commands and data, so that they can be sent over TCP/IP; and, the target extracts the commands and data at the storage device end of the wire.
From end-user point of view, this is how it works:
When an end user or application sends a request for data, the operating system creates the appropriate SCSI commands, which then go through encapsulation and, in some circumstances, encryption. A packet header is added to the resulting IP packets, and the data is transmitted, typically over an Ethernet connection. When a packet is received, it is decrypted and disassembled, separating the SCSI commands and the data request. The SCSI commands are sent on to the SCSI controller, and from there to the storage device. Because iSCSI is bi-directional, the protocol can also be used to return data in response to the original request.
IBM is already shipping a native iSCSI IP storage system, the IBM TotalStorage IP Storage 200i. Analysts say other companies will speed products to market, once the IETF formalizes the standard. Since 2001 , other companies have also introduced ISCSI storage products.
Sunday 29 April 2007
Wondering how the Internet really works? Learn TCP/IP in most enjoyable way.
A must watch for every IT networking and support engineers....
Download the movie from :
http://warriorsofthe.net/movie.html
Thursday 26 April 2007
OSI Model Training Tutorial (1 of 3) : Networking for beginners.
1.OSI Model Training Tutorial (1 of 3)
2.OSI Model Training Tutorial (2 of 3)
3.OSI Model Training Tutorial (3 of 3)
http://www.youtube.com/watch?v=vAY9uD1tb7U (2 of 3)
http://www.youtube.com/watch?v=ds7dWnGkN38 (3 of 3)
Network Attached Storage: NAS Device from VANTEC.
eCDN (enterprise content delivery network)
Overview of Enterprise Storage : For all the storage techies.
1. Direct Attached Storage (DAS).
2. Network Attached Storage (NAS).
3. Storage Area Network (SAN).
Storage Networking Training Video: SAN
Learning Linux : Class room update.
Cool Computer Program: Engineers you will love it.
Wednesday 25 April 2007
Networking and Storage - How much you know ?
Saturday 21 April 2007
Don't *switch* to Linux, *migrate* there :
It is important to remember that Linux and Windows are both operating systems and, as such, don't actually provide any significant functionality of themselves. Rather they provide an environment in which applications, that provide the functionality you require, can run. So the question to consider is does the operating system you are considering support the applications that you need? In general, most of the Linux distributions will support applications that provide equivalent functionality to their Windows counterparts. But mostly they are not the same applications, so there will be a learning curve.
How realistic is it for the average Windows user to install and use a Linux-based OS ?
Most home users surf the Web, do e-mail, take and share digital pictures (well, you will), and trade and print documents with your friends. An open-source operating system does those things. It's safer on the Internet, because it doesn't get viruses.
There's one place open-source falls down, and that's running the very *cheapest* modems, printers, and cameras. If you've still got that ink-jet printer or all-in-one that came "free" with your mail-order Dell, chances are you'd have to replace it with a better model that has Linux device drivers. The same goes for most "software" modems, and Web cams. The good news is your Linux system will come with drivers for the mainstream and high-end devices. You should check one of the Linux compatibility sites or at least ask in a Linux forum before buying hardware that you expect to use with Linux. (linmodems.org, linuxprinting.org, gphoto.org and click on "800 cameras.") If that kind of thing is a show-stopper for you, you're stuck with Windows or Macintosh.
Do you take work home? (I guess not, or you would have had to ditch Windows-98 by now.) Do you run specialized software for stock trading or architectural design? Chances are it only runs on Windows. Do you have a favorite video game? You probably need Windows to launch it.
What are your resources? Can you afford to put more memory in your PC? Replace your printer? Replace a worn out or too-slow CD drive? Can you take a year to make this transition or do you need to make a fully functional office workstation in the next half hour?
Desktop environments for Linux:
As far as applications go, you'll need an office system - OpenOffice.org is probably closest to the Microsoft Office you are used to (except for the macros) but there are others. I like KOffice but I got into it before OpenOffice.org was available. All the Linux distributions provide a web browser - Konqueror is quite close to Internet Explorer and Windows Explorer - or you can use any of the open source browsers, Firefox, Opera, Netscape, etc. Kmail is a lightweight email client but again, any of your preferred open source clients have Linux equivalents, Thunderbird, Opera mail, etc. If you work with a lot of digital images, you will want to get to know The GIMP - it has all the functionality of Adobe's Photoshop without the hundreds of dollars price tag! Like Photoshop, it isn't the most user friendly application but as you learn to use its power, that's a small penalty to pay.
Security on Linux systems is in a different league to Windows - it was always designed as a multi-user networked system, unlike Windows single user standalone desktop origins. All Linux systems have an inbuilt two way firewall that you can configure to your own specific requirements. There have been very few viruses targeting Linux but as its popularity increases, that will undoubtedly grow, though that said, it is much harder to break Linux security. Whether you should include an anti-virus application is a matter of heated debate (which I won't encourage here) but what harm can it do?
The beauty of Linux is that you can start simply, use the GUI, never even see a command line unless you want to. But as you get to know it and grow with it, you can branch out into the more powerful features as you need them.
Should you get rid of Windows XP altogether? My advice would be no, at least to begin with. As you explore Linux, you may come across an application you use that you can't find a Linux equivalent for, so having a Windows system to revert to is a good safety net. You have a licence for it anyway, so apart from the disk space, it's no loss to keep it until you have stopped using it altogether. I still use both for client compatibility, which is another reason you might want to keep XP,
I hope that's given you a few ideas to think about - you've nothing to lose - it's almost all free - as the SuSE Linux installer used to say - Have fun! Good luck.
Thursday 19 April 2007
The power of competition: - Ashwin
Competition: If we look at the world around us, we can easily feel the puslse of competition, whether it is an Athlete striving for Gold in Olympics, a young graduate in opening of a new job , Or a student aiming to top the class and last but not the least , the ever concious common men and women competing to raise the social-standing in the soceity, so the competition is just about everywhere, i don't think any one of us can escape.
Competition, is always healty and in the interest of the betterment of the contry as long as it is in the right spirit, by healthy i mean equal opportunity to all the players who is in race to compete for the best.
Unhealthy competition means pulling one another's leg to win the race, conspiring to erase the opponent, attacking the opposition in a unethical way etc etc. In sports, if we take an example of unhealthy competition we would come across stories of atheletes taking unfair means such as drugs to win the Gold, Hence the spirit of competition taking the ugly shape and that's realy sad.
Unhealthy competition could mean parents pressurising their kids to do what they would like them to, irrespective of what they like to do themselves, this is really sad and not the true side of the competition.
On the positive side, competition has and always paid a great dividens to the people who have embraced it in a right manner, those who have honestly strived and are still striving to give their best without compromising on principles are trully appreciable.
Finaly, competition has direct link with Quality. it is a proven fact that, competition has given rise to "Superior Quality", which has infact benefited the customers with wide range of Quality products and services.
Due to competition, customers have become the KING, every company is aiming to snatch customers from each other, and in a process given the remote control to "common man" the customers , Now we can choose the product we want, which ends the ERA of "MONOPOLY".
Fact reamains, No competition------No Growth.
Wednesday 18 April 2007
Symantec Backup Exec™ System Recovery :(formerly Symantec LiveState™ Recovery)
For details check out this pdf:
http://a248.e.akamai.net/f/248/5462/2h/www.symantecstore.com/v2.0-img/page-builder/Symantec/images/10702265_BUESR_ds.pdf
See the SAN Storage Setup Guide by HP: Build your company's first SAN
http://www.hp.com/sbso/productivity/howto/san/index.html
Perplexed by the word Storage Area Network (SAN) or just don't know how to implement a SAN in your company ? Here's a great guide from HP that tries to make that process clearer.You might also want to check out the new HP StorageWorks portfolio that would help customers consolidate their storage environments.
Digital information is a critical component of business today. It not only continuously grows in volume, but many businesses require that it is available around the clock. Inability to access your information—even to perform a system backup—is no longer an option. Add a shrinking IT budget to these realities, and you're presented with a real challenge. How do you provide efficient storage, management, and availability of your data? The solution can be found in a highly flexible, intelligent, and easy-to-manage storage solution that is also cost-effective: the SAN (Storage Area Network).
As an IT manager, you are faced with critical choices. Do you restrict the type and quantity of information each user is allowed to store and access, potentially limiting their capability to perform their daily activities? Or, do you continue to invest in individual disk drive after disk drive that you connect exclusively to a single server in a Direct Attached Storage (DAS) model that drains man-hours with management and monitoring requirements?
Monday 16 April 2007
Recommended PORT consideration for Firewall/TCP Filtered environment:
Note: According to IANA (INTERNET ASSIGNED NUMBERS AUTHORITY),Ports which we think is Dynamic and Free are not TRUE, Infact when we go through the List of ports given by IANA authority we will find that most ports which we assign are either well known ports OR registered ports and therefore when we specify them in Backup Exec console (Under Network & Firewall) option it does not follow the rule and often get rejected/Refused by the remote server.
According to IANA :
http://www.iana.org/assignments/port-numbers
PORT NUMBERS =(Last update 2006-11-17)
The port numbers are divided into three ranges:
1.The Well Known Ports.
2.The Registered Ports.
3.The Dynamic and/or Private Ports.
The Well Known Ports are those from 0 through 1023.
The Registered Ports are those from 1024 through 49151
The Dynamic and/or Private Ports are those from 49152 through 65535 (Here we need to search for unassigned ports)
As we can see port between 1024 and 49151 is registered and therefore even if we specify these range on the Backup Exec(under tools--options--network & firewall) and similar range on the remote server Firewall/TCP Filerting it may not backup or "refuse to communicate" as seen in the SGMON error.
Backup Exec error Traced in SGMON:
bengine: [3044] 09/12/05 11:53:47 TF_InitMediaServerReverseConnection: Data Connection: Failed to connect to remote address 170.140.236.128:3189,system error message: "No connection could be made because the target machine actively refused it".
This is an clear example of ports been blocked on the TCPFilterting/Firewall except for Port 10000 which is usually the only port opened by network administrator(s) which is used for control connection.
Solution:
To overcome this problem, its recommended to specify maximum FREE (UNASSINGED Dynamic Port) range available and stated by IANA and as per the IANA information it looks like the maximum range available is :5204-5221 which is about 17 ports. Its up to the system administrator to open all the "17" ports or just assign "10" ports. You may refer to IANA website to refer other range.
Specify the range as shown below:
Enable Remote Agent TCP dynamic port range:
5204- 5221
Unless you specify range, Backup Exec uses full range of dynamic ports available which may not work in Firewall/TCP Filtered domain/Environment.
Note: Its recommended to keep range of ports opened instead of just one because being a dynamic port it can be engaged by any other application can cause data connection issues, Therefore atleast keep "10-25" ports opened on the Remote system.
For Ex-
NUMBER OF SIMULTANIOUS BACKUPS =5
NUMBER OF PORTS REQUIRED FOR DATA = 5
Its just an example but make sure at least "10-25" ports opened on remote system Firewall/TCP Filters.
Control connection is always established on port 10000 and once the connection is established the port is FREE to listen to another connection from media server, but the subsequent data backups will need extra port for data pass-through because the previous port is engaged by the first backup job.
Thursday 12 April 2007
Storage Jobs - Storage Area Network or SAN jobs :
Catch this blog:
http://storage-jobs.blogspot.com/
Wednesday 11 April 2007
The Difference Between FTP and HTTP :
URL starts with:
ftp://
In contrast, Hyper Text Transfer Protocol, or HTTP, is a protocol used to transfer files from a Web server onto a browser in order to view a Web page that is on the Internet. Unlike FTP, where entire files are transferred from one device to another and copied into memory, HTTP only transfers the contents of a web page into a browser for viewing. FTP is a two-way system as files are transferred back and forth between server and workstation. HTTP is a one-way system as files are transported only from the server onto the workstation's browser. When http appears in a URL it means that the user is connecting to a Web server and not a file server. The files are transferred but not downloaded, therefore not copied into the memory of the receiving device.
URL starts with:
http://
Connecting using FTP:
The FTP (File Transfer Protocol) utility program is commonly used for copying files to and from other computers. These computers may be at the same site or at different sites thousands of miles apart. FTP is a general protocol that works on UNIX systems as well as a variety of other (non-UNIX) systems.
For the purposes of this Web page, the local machine refers to the machine you are initially logged into, the one on which you type the ftp command. The remote machine is the other one, the one that is the argument of the ftp command.
Getting Started:
To connect your local machine to the remote machine, type :
# ftp machinename
where machinename is the full machine name of the remote machine, e.g., for.test.purpose.edu. If the name of the machine is unknown, you may type
#ftp machinennumber
Anonymous FTPAt times you may wish to copy files from a remote machine on which you do not have a loginname. This can be done using anonymous FTP.
When the remote machine asks for your loginname, you should type in the word anonymous. Instead of a password, you should enter your own electronic mail address. This allows the remote site to keep records of the anonymous FTP requests.
Once you have been logged in, you are in the anonymous directory for the remote machine. This usually contains a number of public files and directories. Again you should be able to move around in these directories. However, you are only able to copy the files from the remote machine to your own local machine; you are not able to write on the remote machine or to delete any files there.
ftp Learning Links:
Active FTP vs. Passive FTP, a Definitive Explanation
http://slacksite.com/other/ftp.html
For complete FTP commands:
http://www.cs.colostate.edu/helpdocs/ftp.html
What is Needed to Use FTP sFTP :
http://www.uic.edu/depts/accc/network/ftp/vftp.html#h1p02
Commands Used to Transfer Files :
http://www.uic.edu/depts/accc/network/ftp/vftp.html#h1p03
Sunday 8 April 2007
How to clear the Browsing HISTORY and the FORMS such as search queries and your search pattern.
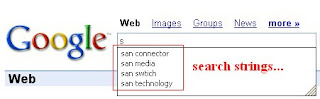
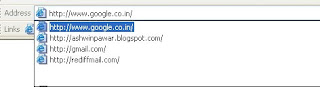
1. Go to Tools Internet Options
1. Go to Tools Internet Options